 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Google Cloud said today it’s adding to Cloud Armor’s capabilities to ward off the growing sophistication and intensity of cyberattacks against its cloud customers.
Google Cloud Armor is the company’s main networking defense service, which is used both internally to protect services including Gmail and YouTube, and externally to safeguard customer’s own applications and services.
As Google Cloud Product Manager Shane Wang and Customer Engineer Naya Dwarakanath explain in a blog post, cyberattacks have evolved beyond isolated distributed denial-of-service attacks. These days, they said, attackers use many more comprehensive techniques, including volumetric flood DDoS attacks, bot attacks and application programming interface abuse to try to take their targets offline.
Google Cloud is thus aiming to thwart such attacks with a range of new features within Cloud Armor. Perhaps the most useful is the new rate limiting capability. Wang and Dwarakanath said customer’s web applications have been frequently targeted by high-volume requests such as HTTP floods that intend to make those services unavailable. To counter such threats, customers now have the flexibility to limit the rate of requests their apps and services can receive.
Cloud Armor’s rate limiting feature makes it easier for customers to curtail traffic to backend resources based on request volume, thereby preventing unwelcome traffic from consuming too many resources and impacting service availability. Cloud Armor now offers two kinds of rate-based rules. Customers can enforce a maximum request limit per client or a maximum request count across all clients based on HTTP request properties. In addition, they can implement a rate-based ban, which rate-limits or temporarily bans requests from connections that exceed a specified limit.
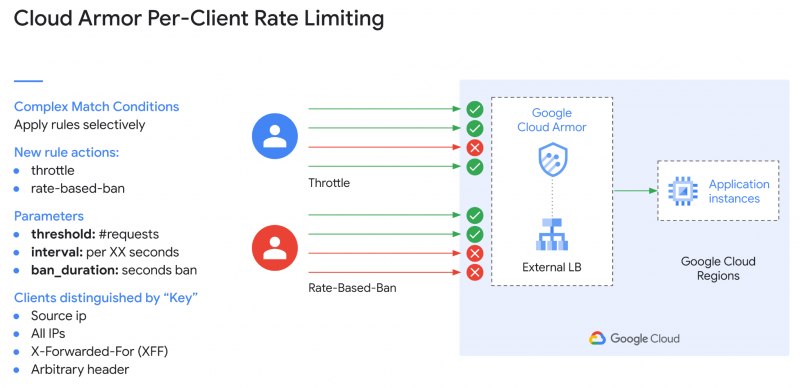
“Customers use Cloud Armor rate limiting to prevent abusive behavior on a per-client basis such as brute force login attempts against their sites,” Wang and Dwarakanath wrote. “Similarly, the rate limiting rules can be applied more narrowly using the CEL-based custom rules language to enforce different rate limits to, for example, different countries where they don’t have any (or many) customers, and use rate limiting to throttle those attacks.”
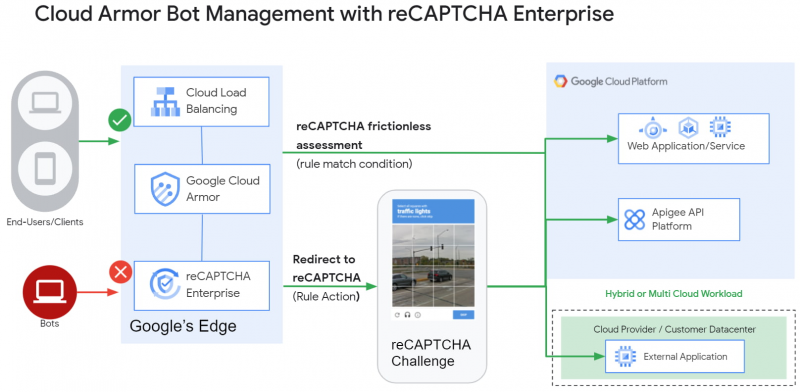
Meanwhile, to deal with bot attacks, credential stuffing, scraping and inventor hoarding attacks, Google Cloud is making reCAPTCHA Enterprise generally available. Cloud Armor now integrates with reCAPTCHA Enterprise to identify bots and either block their access to a certain service, or redirect them to alternate content based on their risk score.
Alternatively, customers can elect to have suspected bots solve a reCAPTCHA challenge when they trigger certain rules. In such cases, the user would have to pass the challenge to gain access to the requested application.
A third new feature announced today is updated preconfigured web application firewall rules that are designed to help customers mitigate the top ten vulnerabilities identified by the Open Web Application Security Project.
“With this preview release, customers are able to deploy the latest industry standard WAF signatures in Cloud Armor security policies to selectively filter Layer7 traffic and protect their web apps and services from exploit attempts such as SQL injection (SQLi), cross-site scripting (XSS), or remote code execution (RCE),” Wang and Dwarakanath said.
Google Cloud Armor further empowers companies to employ a “defense in-depth strategy” with the preview availability of Google Cloud Threat Intelligence for Cloud Armor. This service provides ready-to-use and continuously updated threat intelligence for customers to enhance their network security according to the latest threats and techniques they can expect to face.
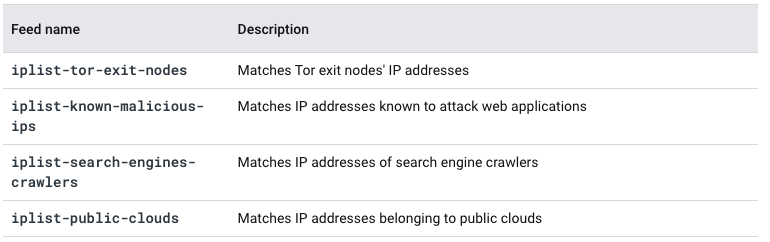
“With the new Google-curated Threat Intelligence, customers can configure security policies to filter traffic based on the following four categories: Tor exit nodes, malicious IPs, bad bots, and public cloud endpoints, with more categories planned in upcoming releases,” Wang and Dwarakanath explained.
Meanwhile, Google said it’s extending Cloud Armor to cover additional types of workloads through the introduction of new edge security policies and support for proxy load balancers.
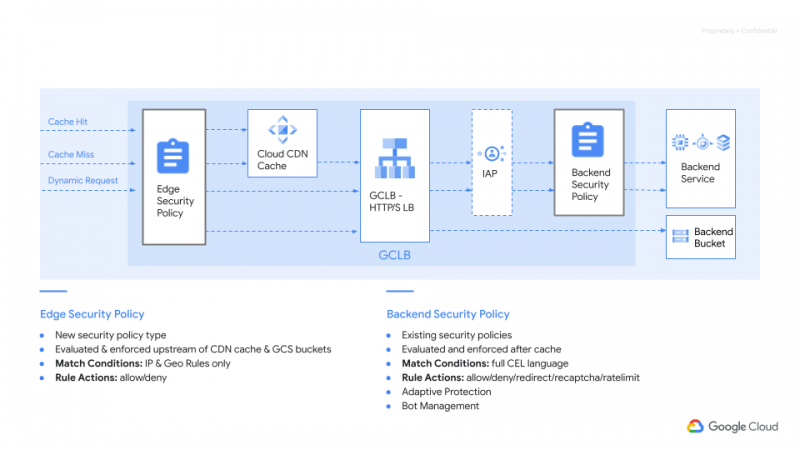
In a second blog post, Cloud Armor Senior Product Manager Emil Kiner and Network Security Portfolio Product Manager Gregory Lebovitz said the new edge policies will help extend its protections to workloads that rely on Google Cloud’s Content Delivery Network, Media CDN and Cloud Storage services. Added to that, Cloud Armor gains support for the TCP Proxy and SSL Proxy load balancers, helping to protect against malicious traffic that targets them.
THANK YOU