 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A newly discovered service on the dark web has been found to allow cybercriminals to easily add malware to legitimate apps.
Detailed today by researchers at ThreatFabric B.V., “Zombinder” was discovered while researching several cases of threat actors using a form of Android banking malware known as Ermac. As the researchers dug further, they uncovered a campaign that employed several different types of malware targeting Android and Windows users, including Erbium, the Aurora stealer and Laplas “clipper.”
Campaigns using various forms of malware installed on Android apps are nothing new and are sadly all too familiar in 2022, but where the story gets interesting is that the researchers traced the campaign back to a third-party darknet service provider, which they dubbed Zombinder.
Advertising on the dark web as an application programming interface binding service, Zombinder launched in March 2022 and is now believed to be used by different threat actors. In an advertisement on a hacking forum, those behind the service pitch it as offering a universal binder that would allow malware to be bound with almost any legitimate application.
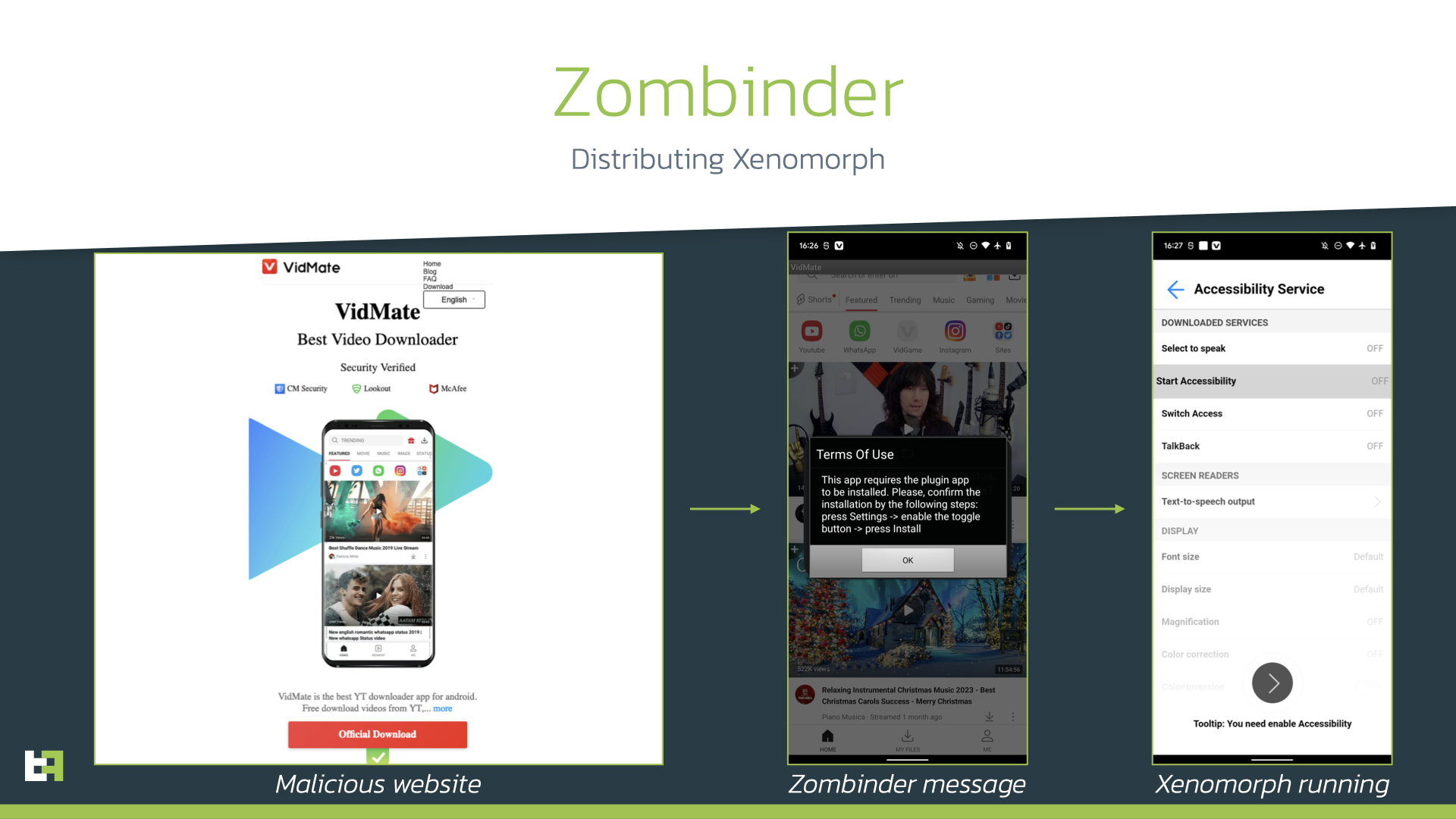
In its latest campaign, Zombinder has been distributing the Xenomorph banking malware under the guise of a VidMate application. Distribution involves the modified application being advertised and downloaded from a malicious website that mimics the original website of the application, with the victim tricked into visiting the site through malicious ads.
Varying from other malicious campaigns where apps don’t work, the Zombinder-infected application works as advertised. The victims remain unaware that they have also been infected by malware.
Although Android apps are the core focus of Zombinder, those behind the service also offer binding for Windows apps. Potential victims who download an infected Windows app also download the Erbium stealer, a popular form of Windows malware that steals saved passwords, credit card details, cookies and cryptocurrency wallet data.
“Android users can avoid Zombinder and similar malware by avoiding third-party app and APK download sites,” Paul Bischoff, privacy advocate with tech research company Comparitech Ltd., told SiliconANGLE. “Developers rarely upload their apps to these sites, so most of them are put there by third parties, likely without permission.”
Bischoff added that users should stick to Google Play or another official app store to help ensure they’re getting a legitimate version of the app. Similarly, users should not download an APK that someone sends them as a link or attachment in a message or email.
THANK YOU